Firewall Fazer um comentário
eScan’s in-built firewall monitors and logs both incoming and outgoing network activities in the system and protects it from all network based attacks. There are different set of rules such as Trojan Rule, Zone Rule, Expert Rule, Application Rule, Trusted MAC Address and Local IP List that can be used to either allow/block any incoming and outgoing traffic.
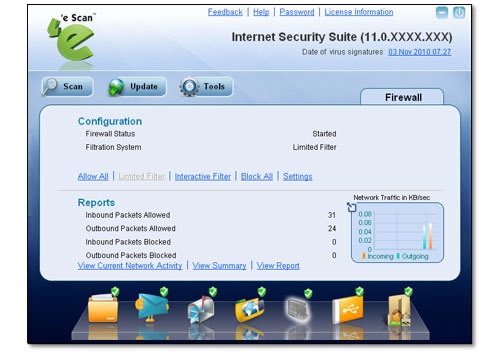 |
The application has two tabs; Active Connections and Established Connections. In Active Connections tab all connections that are active at any given point of time are displayed. In Established Connections, only the connections that are established are displayed.
The Process, Protocol, Local Address, Remote Address and Status of each connection are displayed.
The application gives details on the process associated with each TCP/IP address and port. The process name, the task associated with the process and the name of its developers are displayed.
